- Identifying security threats
- Troubleshooting undesirable network behaviours
- Identifying network congestion
- Identifying data/packet loss
- Forensic network analysis
Packet capture can be performed in-line or using a copy of the traffic that is sent by network switching devices to a packet capture device.
Full Packet Capture
Entire packets or specific portions of a packet can be captured. A full packet includes two things: a payload and a header. The payload is the actual contents of the packet, while the header contains metadata, including the packet’s source and destination address.
Packet Capture Analysis
Analysis of packet capture data typically requires significant technical skills and often is performed with tools such as Synesis packet capture tool and other packet capture tools like Wireshark but Wireshark stars dropping packets after 10G.
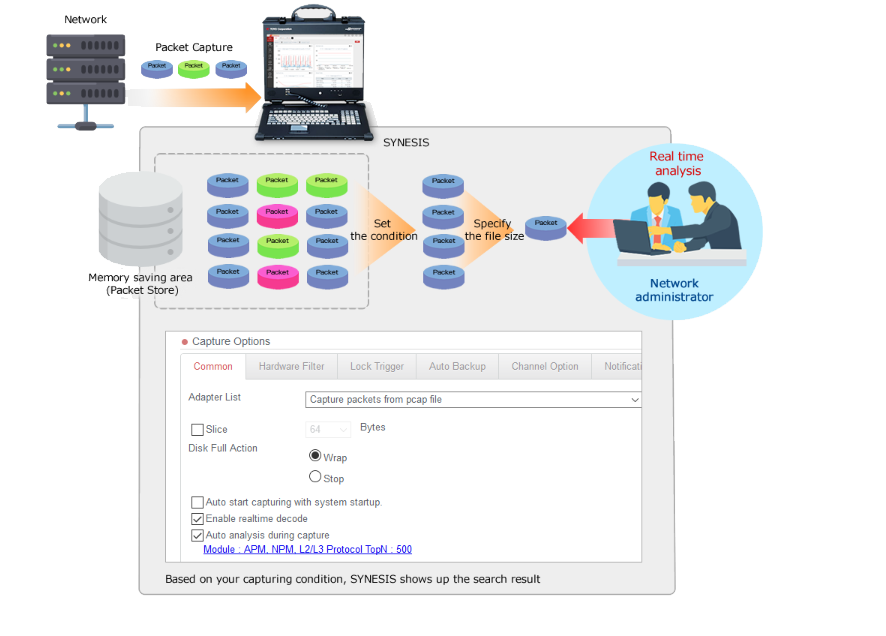
Synesis packet capture tool
- SYNESIS supports the 10M/100M/1G/10G/100G network and captures wire-rate traffic data without packet loss.
- Once SYNESIS starts capturing, data is automatically saved in SYNESIS memory area(Packet Store).
- You can save the captured data as trace files with designated conditions schedule, IP addresses, or protocols.
- You can analyze each trace file (PCAP format) with your analysis tools, also with SYNESIS own analysis